Web - Code Check(湖湘杯)
源码分析
从get请求id参数中解密出正确id,然后执行sql查询语句,将查询结果返回到数组
decode函数:
将传入的data(也就是get方法的id参数)解2次base64后
使用aes-128位 CBC模式 填充为ZeroPadding 解密,key为ydhaqPQnexoaDuW3 iv为2018201920202021
检测解密后的数据后7位是否为hxb2018
如果不是则输出<script>window.location.href="/index.php";</script>
也就是js跳转到/index.php
否则,返回去除首尾空格以及末尾hxb2018后的明文数据
temper
1 | import base64 |
Misc - Disk(湖湘杯)
ftk打开发现有4个flag文件,保存下来是二进制,转十进制然后转ascii
https://www.jianshu.com/p/62c629c076ad
其实直接010打开搜索flag就可以发现有ads隐写了,不过用工具更方便
Reverse - Replace(湖湘杯)
upx脱壳,我是直接copy算法出来爆破解决的
1 |
|
而dalao都是直接看破算法的本质 Orz
要求table[input[i]] == atoi(data[2i]+data[2i+1])^0x19
https://www.anquanke.com/post/id/164604#h2-5
Reverse - HighwayHash64(湖湘杯)
分析
这种题一般都会修改默认的加密参数,所以编译时需要修改默认的c语言文件
基本上参考dalao的方法,编译修改过的模块,用python爆破
第一个判断,用来验证 flag 的长度,经过爆破,确定 flag 的长度为 19(也可动态调试获得0x13)
第二个判断,用来验证 flag 格式内的值,也可以爆破,来确定 flag 格式内的值
脚本
1 | from highwayhash import * |
趣味密码
+++++ +++++ [->++ +++++ +++<] >++.+ +++++ .<+++ [->– -<]>- -.+++ +++.< ++++[ ->+++ +<]>+ +++.< ++++[ ->— -<]>- -.+++ ++.++ ++++. <+++[ ->— <]>– —-. <+++[ ->+++ <]>++ ++.<+ ++[-> —<] >—- .<+++ [->++ +<]>+ ++++. +.<++ +[->- –<]> –.++ +++.- —– -.<++ ++++[ ->— —<] >.<++ ++++[ ->+++ +++<] >++++ +++++ ++.++ +++++ .—- —– .++++ .—- -.<++ +[->+ ++<]> +++++ .<
一段bf代码,在线解密得到flag
flag{interestingCrypto}
你玩英雄联盟吗
是一个流量包,wireshark打开,搜索flag,发现post了一个压缩包
导出发现有密码,但是可以明文攻击
解压出来的flag.zip是伪加密,修复后解压出一个反色的二维码
反色后在线解析得到flag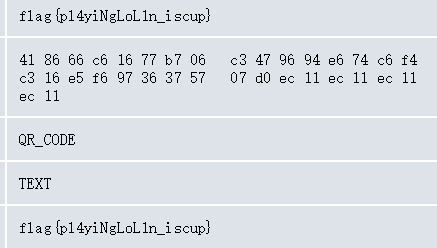
紫霞仙子
分析
jpg文件后隐藏有一个zip文件,提取出来后发现是伪加密,解压出一个包含rgb值的txt文件,有74884行
在数字帝国查询,得到分解因式的结果2x2x7x193
猜测高度宽度为386,194
于是用搜索引擎查找rgb值转图片,得到一个转换脚本
手动删除txt文件的括号后使用脚本转换
脚本
1 | from PIL import Image |

